Do you need cyber security insurance?
ARE YOU PREPARED? Over the last year and a half, if we have learned anything, we know that the pandemic caused a global shift to remote and hybrid work. It forced organizations to review the way they operate practically overnight, with little to no preparation and...
Network Assessments! Do you know how it works?
An annual network assessment provides a lot of value to your business. A variety of tools are run on the systems that collect and analyze key data points. This data is then used to create easy to read reports. The assessment reports can help identify risks such as: -...
The BUZZ is all about the “DARK WEB”
What is the dark web? The dark web is a part of the internet hidden away from normal users. Special software is needed to even get to it. A regular browser like Edge or Chrome will not be able to take you to it. The dark web itself is not a single place where you can...
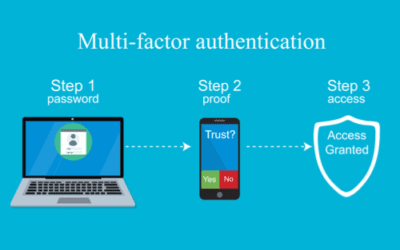
2 Factor Authentication
What exactly is two factor authentication (2FA)? 2FA is a second layer of protection beyond just a password, when you log into an online account. This is used as extra security to keep unwanted people from accessing your information as easily. Passwords have always...
What actions have you taken to stop the spread of infection in your IT environment? Do you know how to protect an infected machine, and provide remediation and rollback? If you don’t know the answer…It’s EDR…
What is EDR?EDR stands for Endpoint Detection and Response. It is a comprehensive security product that protects your computer from viruses, ransomware, and other malware. Scanning currently running processes for malicious activity and behavior. Stopping those...
Don’t think it can’t happen to you! “Protect yourself and do your research before clicking on links”
In a recent article published by the FBI - Sacramento Calif. on 7:39 PM EDT March 20, 2020, there are hackers claiming to provide information on the virus; donating to a charity online or through social media; contributing to a crowdfunding campaign; purchasing...
If all your data were lost, could your business survive?
One of the least thought about aspects of running a business is keeping backups of your vital data. How would you feel if someone accidently erased your wedding photos or photos of the birth of your child? Most likely you would feel a void that would indescribable –...
Reasons for choosing MSP over “In-house” IT
Before we delve into why you might want to pick using an MSP service, we should go over what MSP stands for: Managed Service Provider. They are IT companies built to provide technology services for businesses of various size and industry types. One of the main...
What Our Customers Have Told Us
Over the last few years in talking to customers, there are several common requests: Budget and cost certainty Security from virus, ransomware and other cyber attacks Reliable and restorable backups Maximum uptime All very important points to be sure. Our...
How Much One Click Can Cost Your Business
Cyber attacks cost small businesses between $84,000 and $148,000.
Windows 7 End of Life Consideration
In a previous blog we discussed the looming Windows 7 end of life date, January 20, 2020. Over the next 15 months, most businesses are going to have to make some strategic migration decisions. One of the biggest questions is going to be whether to upgrade existing...
Premise vs Cloud Telephone System! Part 2 – True cost comparison
In our previous blog we highlighted some areas where the total cost of ownership warranted some research into both a premise and cloud telephone system. In part 2, we will highlight some areas where the cloud my be more advantageous for the customer If you are...
Don't Be Shy
Drop us a line anytime and one of our team members will be happy to help you
Subscribe To Receive Industry Updates
Sign up to receive updates, directly from us.